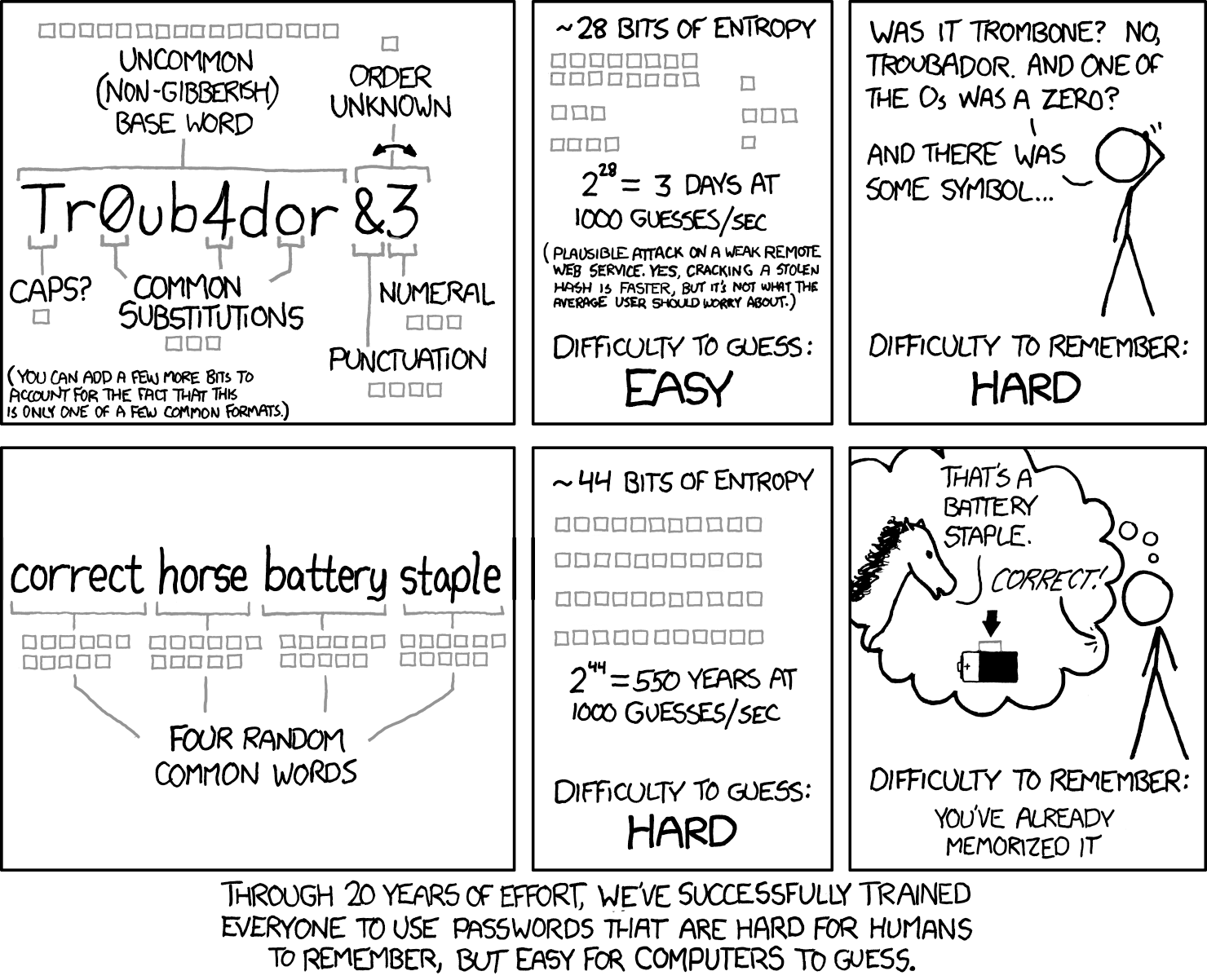
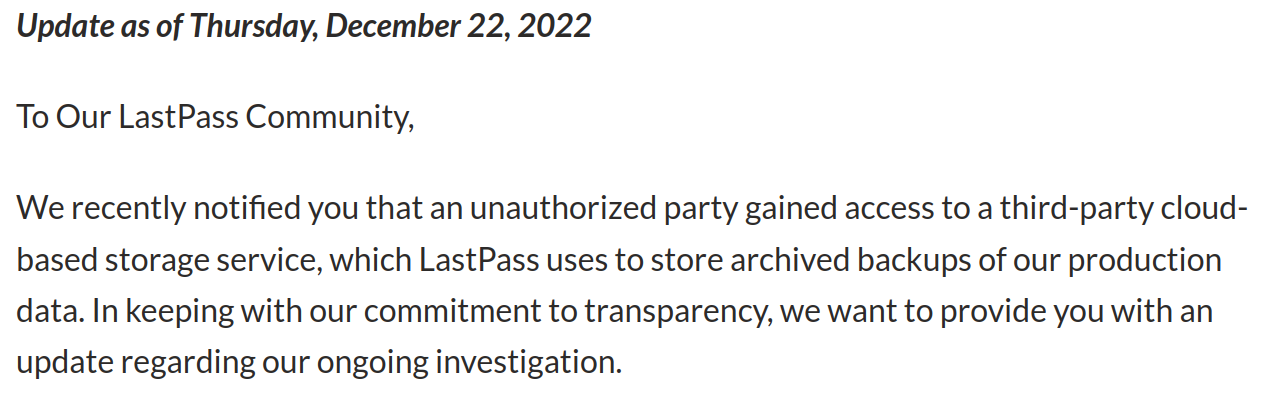
There are several good password managers out there, all prime targets for crackers and hackers, obviously. Probably no need to spend part of your holiday vacation moving things to a new manager out of misplaced panic. From the Last Pass blog (I know, compromised companies are not always forthcoming with information, but Last Pass has a vested interest in being fairly honest.)
As a reminder, LastPass’ default master password settings and best practices include the following:
- Since 2018, we have required a twelve-character minimum for master passwords. This greatly minimizes the ability for successful brute force password guessing.
- To further increase the security of your master password, LastPass utilizes a stronger-than-typical implementation of 100,100 iterations of the Password-Based Key Derivation Function (PBKDF2), a password-strengthening algorithm that makes it difficult to guess your master password. You can check the current number of PBKDF2 iterations for your LastPass account here.
- We also recommend that you never reuse your master password on other websites. If you reuse your master password and that password was ever compromised, a threat actor may use dumps of compromised credentials that are already available on the Internet to attempt to access your account (this is referred to as a “credential stuffing” attack).
If you use the default settings above, it would take millions of years to guess your master password using generally-available password-cracking technology. Your sensitive vault data, such as usernames and passwords, secure notes, attachments, and form-fill fields, remain safely encrypted based on LastPass’ Zero Knowledge architecture. There are no recommended actions that you need to take at this time.
However, it is important to note that if your master password does not make use of the defaults above, then it would significantly reduce the number of attempts needed to guess it correctly. In this case, as an extra security measure, you should consider minimizing risk by changing passwords of websites you have stored.